Abstract cyber security with phone and icons concept And internet protection systems Data importing or exiting various devices. 8551663 Vector Art at Vecteezy

Cyber Security and Mobile Device Management - Cyberhunter Cyber Security | Network Security, Cloud Security & Website Security | Penetration Testing | Vulnerability Assessments | Threat Hunting













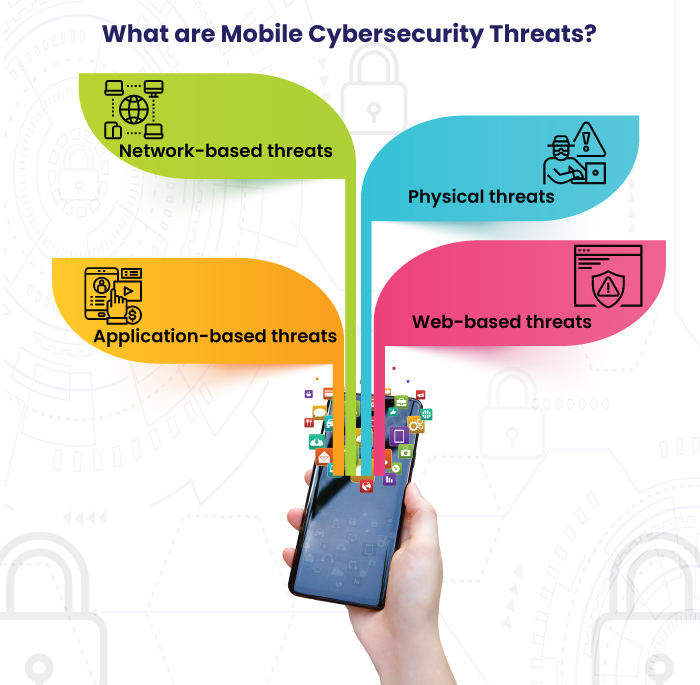


.jpg)